Email phishing attacks are not new, but they are increasing every quarter as cybercriminals are encouraging more and more people to divulge their financial and sensitive data for reporting purposes. identity theft The sender's email address is spoofed to give the impression that it is from a trusted source. According to US Security Solutions Provider FireEye's Email Threat Report, Microsoft is the most counterfeited brand, accounting for nearly 30 percent of detections. Apple, PayPal and Amazon are also on this list, each in the 6-7% range.
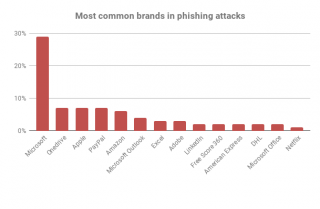 (Image credit: Future) Attackers don't limit their activities solely to the commercial sector. The top 20 brands used in phishing attacks include personal services like Netflix, LinkedIn, Amazon, and Free Score 360.
(Image credit: Future) Attackers don't limit their activities solely to the commercial sector. The top 20 brands used in phishing attacks include personal services like Netflix, LinkedIn, Amazon, and Free Score 360.
The most common brands detected during phishing attacks.
Microsoft - 29%OneDrive - 7%Apple - 7%PayPal - 7%Amazon - 6%Microsoft Outlook - 4%Excel - 3%Adobe - 3%LinkedIn - 2%Free Score 360 - 2%American Express - 2%DHL - 2%Microsoft Office - 2%Netflix - 1%
Source: FireEye
Phishing has increased, with an increase of 17% in the first quarter of this year.
The security company recorded a 17% increase in phishing attacks in the first three months of this year compared to the last three months of last year. FireEye has been the scene of numerous attacks involving emails associated with a Microsoft Office 365 account. Ken Bagnall, FireEye's vice president of email security, said the threat actors were doing his homework. "We are seeing new variants of impersonation attacks targeting new contacts and services within organizations," he said. The report says that HTML attachments and phishing pages are other popular phishing attack mechanisms in Q2018 because HTML attachments are not hosted; They can escape detection and appear very convincing. In 26, FireEye reported that URL attacks had surpassed attachment attacks as a means of delivery. The company has seen a XNUMX% quarter increase in the number of malicious URLs using HTTPS, indicating that malicious actors are taking advantage of the current consumer perception that HTTPS is a "safer" option. to use online. Phishing pages that require user interaction, such as Standby, Captcha, Display Links, and Graphical buttons, as well as links to malicious documents, reinforce the apparent authenticity of the page.
This email is not coming from your CEO
Identity theft attacks, such as CEO fraud and professional email, also showed a steady increase during the quarter and the trend indicates a continued increase in the second quarter, as actors imitate leaders and executives to deceive to employees, allowing them, for example, fraudulent transfers. "The danger is that these new targets may not be prepared or have the necessary knowledge to identify an attack... The targeted organization thinks they paid a legitimate bill when the transaction was made to a bank account. The striker," Bagnall said.

 (Image credit: Future) Attackers don't limit their activities solely to the commercial sector. The top 20 brands used in phishing attacks include personal services like Netflix, LinkedIn, Amazon, and Free Score 360.
(Image credit: Future) Attackers don't limit their activities solely to the commercial sector. The top 20 brands used in phishing attacks include personal services like Netflix, LinkedIn, Amazon, and Free Score 360.