
It's been a busy week for the Lapsus€ hacking and extortion collective. He first leaked what he claimed was LG Electronics employee account information, such as the source code for multiple Microsoft products.
Hours later, the group also posted screenshots indicating that they had breached the identity and access management company Okta. Word of the possible breach spread rapidly online.
Okta provides a single sign-on service for large organizations that allows employees to log into multiple systems without requiring a separate password for each system. An Okta hack could have potentially serious consequences for customers of the service.
Okta's reply
Okta issued a preliminary statement Tuesday morning, asserting that the screenshots posted by Lapsus€ stem from "an attempt to compromise the account of a third-party support engineer working for one of our contractors" that occurred in the month of January of the current year.
A second statement from David Bradley, Okta's security officer, gave more details about the "misguided attempt" to breach the support engineer's account.
While assuring customers of the service that "the Okta service has not been hacked and continues to be fully operational," he also conceded that a forensic investigation found that "there was a 5 day time window between January XNUMX and XNUMX, thousand twenty-two, where an attacker gained access to a support engineer's laptop." Bradley, however, insisted that "the potential impact on Okta service customers is restricted to the access that support engineers have," noting in particular that the hacker suite cannot download service customer data. and does not have access to the access keys.
Independent security scholar Bill Demirkapi provided more details to TechRadar Pro by email. He explained that the external support engineer appeared to work for SYKES Enterprises, Inc, now confirmed by Okta, and that "due to the access these support staff had, Lapsus € was able to breach Okta's internal Slack, Jira, and administrative backend." . access panel used to assist customers of the service ". He added that" now, it does not seem that Lapsus € still has access to the Okta environment ".
On Tuesday afternoon, Lapsus€ responded to Bradley's statement on his Telegram channel, questioning his characterization of the attack as "failed." Lapsus€ also claimed that Okta stored AWS keys in Slack and called out the company for waiting so long. to notify its users of the January mishap.
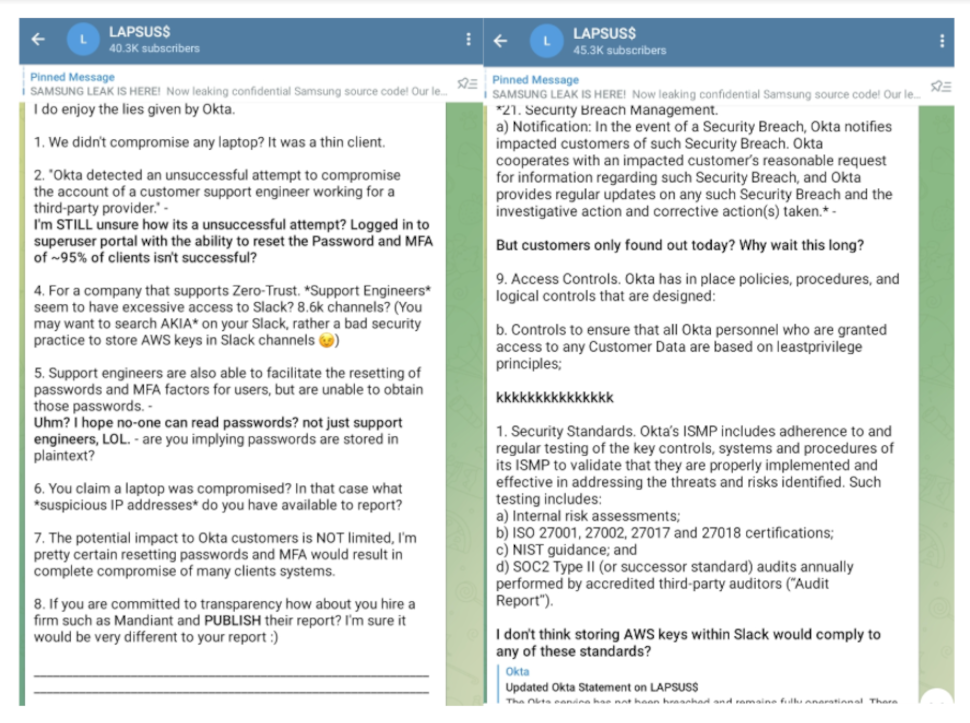
Bradley has since acknowledged that "a small percentage of service customers - around XNUMX% - were potentially harmed" by the mishap and their data may have been "accessed or processed", although he continues to insist that "there is no corrective action that our service customers should take."
In a separate post, Bradley laid out a timeline for the mishap and addressed Lapsus€'s previous reference to a "superuser" portal, dismissing claims that it gave the group "divine access" to customer accounts of the service. Instead, Bradley clarified that SuperUser Portal "is an application developed with least privileges in mind to ensure that support engineers are given only the specific access they need to perform their roles."
Okta has faced criticism from both Lapsus€ and the security industry for not discovering the January mishap sooner. Predictably, the leak unsettled investors, causing Okta's share price to drop, as did Raymond James Equity Research's downgrade.
Who is Lapsus€?
Despite the chaos caused by its members this week, Lapsus€ is partially new to the cybercrime scene. The hacker collective sprouted late last year, but has already cracked big names like Microsoft, Nvidia, Samsung and Ubisoft.
On Tuesday, Microsoft released a report on Lapsus€, noting that the outfit is unusual in promoting its activities on social media and clearly recruiting employees who are ready to give access to companies they want to hack.
While winning over the band's online fans, Lapsus' social media presence is also working to its detriment. Lapsus€ promoted the attack on Microsoft on social media as it unfolded, with Microsoft stating that it "accentuated our action by allowing our team to step in and disrupt the actor's operation, thus limiting further impact."
Bloomberg reported on Wednesday that two of the Lapsus€ members are believed to be teenagers, one living near Oxford in the UK and the other in Brazil. The British teenager, known by the pseudonyms 'White' and 'Breachbase', was identified by cybersecurity scholars in mid-XNUMX after leaving a trail of information about himself online. He has also been tricked by other hackers, who claim that he has almost €XNUMX million worth of cryptocurrency.
On Thursday, the BBC reported that 7 people between the ages of 7 and XNUMX had been arrested by City of London police in connection with an investigation into Lapsus€, although it was unclear whether the teenagers mentioned by Bloomberg were part of the group. The detainees. Since that time, all XNUMX have been released under investigation.
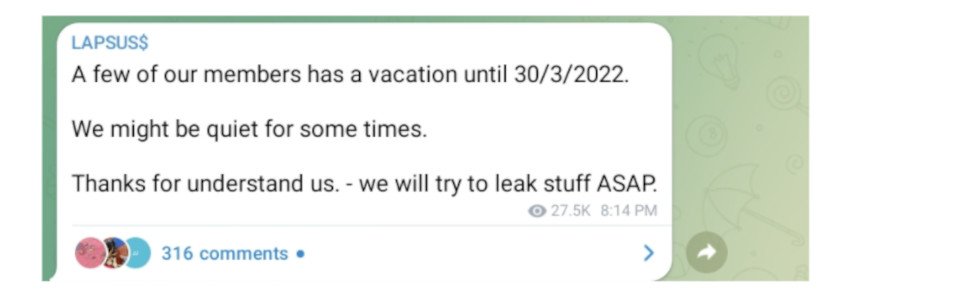
On Tuesday night, Lapsus€ announced that the band "may be quiet" for a while, as some of its members are going "on vacation until 30/03/2022." Although the band promised to "try to leak things as soon as possible," in light of the recent arrests, the collective may be taking a longer hiatus than expected.
Despite their youth, the teenage members of Lapsus€ are exaggeratedly efficient. As Microsoft noted, Lapsus€ "understands the interconnected nature of identities and trust relationships in modern technology ecosystems and is targeting telecommunications, technology, IT services, and support companies to leverage their access from within an organization to access partner organizations or distributors".
How companies can protect themselves
Microsoft's report contained advice for companies on how to guard against Slippage attacks. The report notes that "multi-factor authentication (MFA) is one of the primary lines of defense against" the hacker community. But he also noted that insecure methods such as SMS MFA are not enough, as Lapsus€ has been implicated in SIM swapping attacks to access SMS MFA codes.
Since Lapsus€ frequently steals credentials through social engineering, Microsoft also advised raising employee awareness of these types of attacks. Other suggestions included using "modern authentication options" for VPNs and ensuring that incident response communication channels are "closely monitored for unauthorized participants" in the event Lapsus€ tries to infiltrate.
In addition, Microsoft has provided a set of resources that companies can use to help "warn, track, and respond" to Slipper€ attacks or similar mimicking sets.